 |  |

 |
Shaman > Setup > Remote server setupShaman Setup is a graphical utility that supports end users with SSH Key management, including enabling or disabling OpenSSH access to remote servers. The private side of the SSH Key pair always remains encapsulated in a cryptographic token.
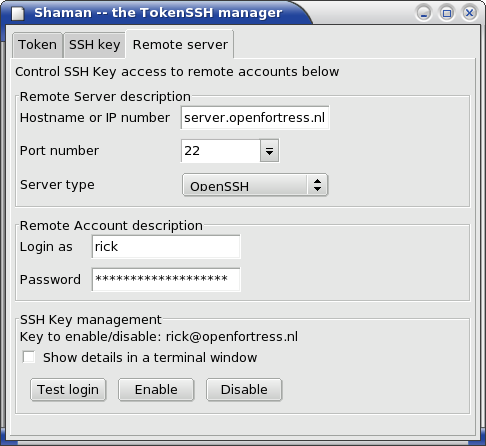
Using the Token and SSH key tab, a current token and an SSH Key on that token were selected. The Remote server tab is used to enable or disable access to a Remote server for this combination. As soon as the test login succeeds, the token-based SSH Key is ready for everyday use on the Remote server it was tested on.
Remote Server description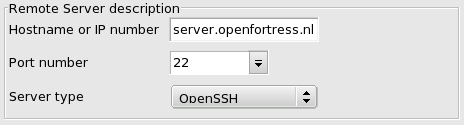
This part of the window is used to setup the remote server for which access should be managed. The first field can be used to enter either the hostname or IP number. Name resolution works through your local infrastructure. The port number is only different from 22 when your administrator instructed you explicitly to change it. The server type determines what kind of remote system you are accessing. This may be the open source product OpenSSH or the commercial product; since you are using OpenSSH locally, the default assumption is that your remote server also runs that software. Remote Account description
This part of the window is used to tell what account on the remote server you are managing the access to. The loginname is needed to identify that account, and a password is needed in situations where no access based on an SSH Key is yet possible. SSH Key management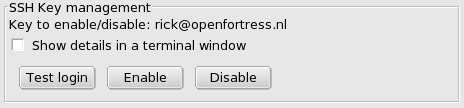
This part of the window allows you to control access to the remote server described under Remote Server description, and on that server specifically the account entered under Remote Account description. Note how the interface repeats the current SSH Key that was selected under the SSH Key tab. The three operational buttons are Test login, Enable and Disable. If any of these fail in an unknown manner, please switch on the Show details toggle. It will display its output in a popup window, from where you can copy/paste it to provide your administrator or helpdesk with details that are useful to them. Enable remote access with the SSH Key
This button is used to grant access to the remote server with the current SSH Key. To actually get into the remote server and install the proper settings under the selected account, it is necessary to gain access first. The system administrator must have set this up, by allowing you to use your password. The password is not needed for the other operations. The Enable operation will return explicit information on success or failure. Read this carefully, and even if success was reported be sure to do a Test login to test it in practice. Disable remote access with the SSH Key
This button is used to revoke access to the remote server with the current SSH Key. This assumes that some means of accessing the remote server currently exists, namely with the SSH Key that is to be disabled. To ensure that this works, it is a good idea to do a Test login before trying to disable the SSH Key. After the task completes, a clear indication of success or failure will be shown. If success is reported, it means that the current SSH Key was removed from the remote server. Please note that there may still be other SSH Keys, possibly on the current token, that are granted access to the remote server. So, even if success is reported you will want to do a Test login on this remote server. If your intention is to revoke access to all remote servers at once, for example because you suspect key compromise due to physical tampering with your token, you could also use the Destroy button under the SSH Key tab. Even then it is a good idea to first cleanup and disable access to all remote servers, just to clean up unused rubbish. Test if login is possible
This button can be used at any time to see if a login without password is possible. Note that regardless of whether you provided a password, it will not be used. Everything else will be used, including the token and any other public keys that may be available to SSH at the time of login. Although it is the ideal test to see if access to a remote server is possible or fully blocked, it can also be somewhat confusing. Disabling one SSH Key may succeed, but another SSH Key may still be enabled at that time, and lead to successful remote access. If you disabled an SSH Key successfully and you can still login, hunt for other SSH Keys that may be the cause of this. If you experience inconsistencies getting in, and receive reports about failing agents, you may have to look at the file As soon as the Test login succeeds on all remote servers and accounts of interest, you can quit the Shaman and resort to everyday use of SSH. |
 |  |
 intro
intro